Data Backup and Recovery
How to Prevent Data Loss in 5 Practical and Easy Ways
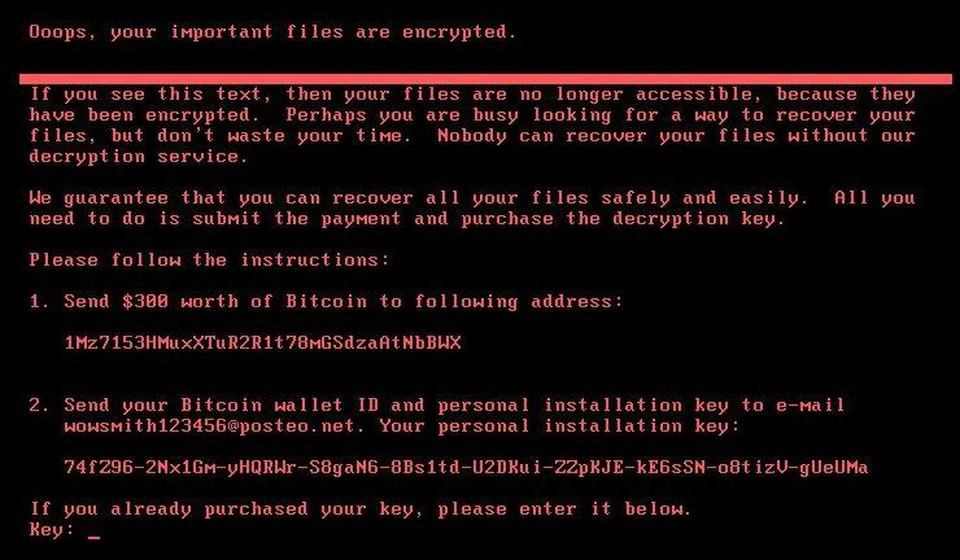
Ransomware Petya is one scary way you can lose business data and money.
Today’s ever changing IT world, it’s hard for small businesses to keep up with the latest security best practices.
If you are a business owner today, you’d know protecting your data and having a recovery plan is a must.
According to worthinsurance.com, about 77% of businesses have no plan for incident response.
Before we consider data recovery, we need to discuss 5 security practices to reduce the risk of data loss.
#1. Keep Your Hardware Protected as Much as Your Software
When everyone thinks of data security, they think of strong software hard to attack.
The reality is however you’ll need to consider protecting your endpoint devices such as computers first.
Here’s some ways to do it:
-
1
Put a circuit breaker in place - Computers can be susceptible to damage when a power surge occurs
-
2
Use USB fingerprint devices to protect against theft and unauthorized access
-
3
Use anti-theft equipment that alerts the owner of any unauthorized and physical movement of a device
-
4
Never leave your endpoint devices unattended - especially in places such as a coffee shop where theft is easy. We recommend you take the laptop with you during any movement within a physical environment
Many USB fingerprint devices are listed on amazon with the $20-$50 range. Anti-theft equipment such as Prey offers webcam screenshot capabilities to capture thefts. Absolute only has a paid plan and can lock down devices if they are stolen. We recommend you install such software on more expensive devices where you’d usually store important data
#2. Clean Up Your Workspace
This is one not many consider. Keep food and drink away from your devices in case of an accident. Ideally you should make sure employees keep up with the practice.
Other than that, it keeps your space looking professional and sound, allowing you to do your best work with confidence.
Not only do you have to clean your desk, but you can avoid human error by cleaning up your virtual workspace. Especially considering that you can easily delete or lose track of sensitive information. Here’s some ways you can do that:
-
1
Delete any unused apps - they occupy much more space than you think
-
2
Use cloud storage to prioritize important data and files tax, projects, presentations, reports, and backups.
-
3
Use disk cleanup tools to delete unnecessary files. There are various options available, such as CCleaner, or built-in utilities provided by your operating system.
-
4
Delete intellectual property no longer in use
Overall, we recommend following these suggestions because it requires little know-how to do.
#3. Use Strong Passwords
We hear it everywhere, we even see how required it is when signing up on different platforms. However, according to statistica.com, only 31% input a unique password at work according to statistica.com. More employees are relaxed when creating passwords. It’s why so many businesses become targets of data leaks.
Either way, here is a recommended guideline of how you should structure your password policy in your company:
-
-
Password length of 8 characters
-
-
Use upper and lowercase
-
-
Use at least one special character such as $, #, @ ?
-
-
Don’t repeat numbers in a row (ex. john333)
-
-
Don’t use your name
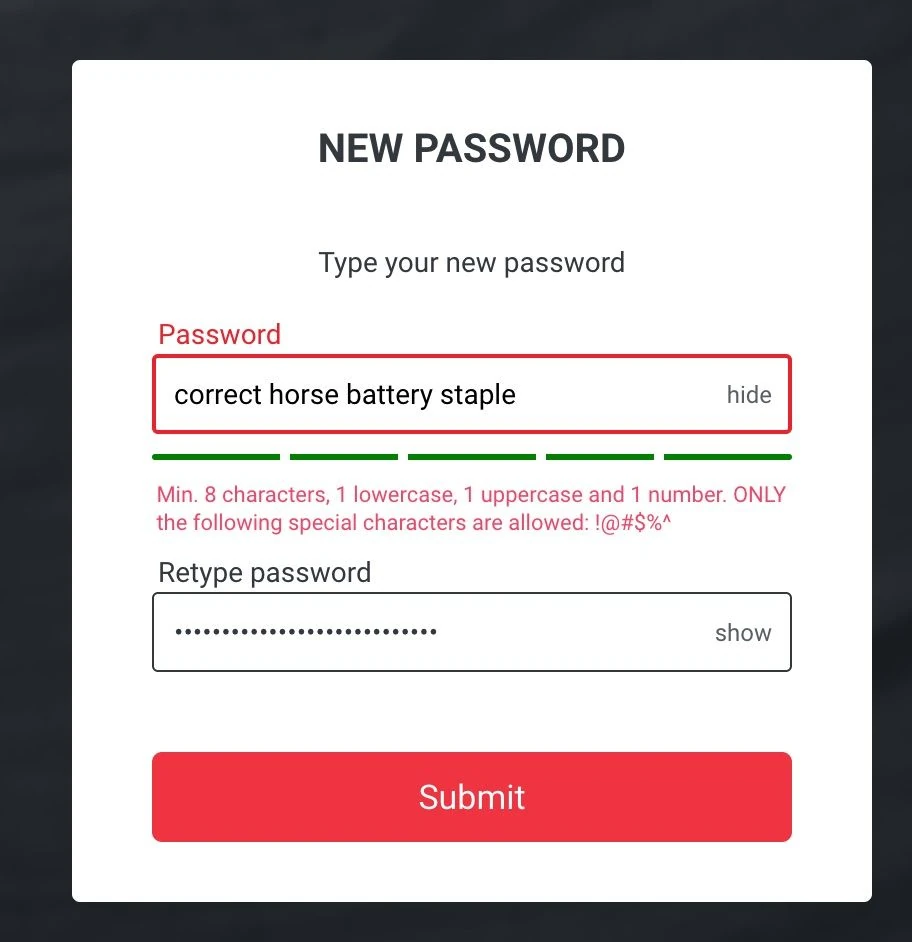
Websites such as this one prioritize your safety over password guessing. Image courtesy of Alan Franzoni (https://www.franzoni.eu/)
We recommend that your employees are aware of this as well. Write this down as you will catch yourself breaking at least one or two of these rules when creating passwords for critical data.
#4. Use Data Loss Prevention Tools
Data loss prevention tools give you complete control over your data. Naturally, they are one of the safest security measures to prevent data loss. Data loss prevention DLP software usually:
-
-
Block unauthorized users requesting access to critical systems
-
-
Offer endpoint protection, IPS, and anti-malware systems
-
-
Identify sensitive data such as personally identifiable information (PII), financial data, intellectual property, and healthcare records
-
-
Constantly monitor file transfers, emails, network traffic, and printing attempts among other data activity types.
-
-
Ensure that you are keeping up with regulatory compliance such as, HIPAA and PCI DSS
You can use tools such as McAfee DLP Endpoint, Microsoft Purview Data Loss Prevention which integrates with Microsoft 365. Forcepoint suits larger businesses with complex needs. Proof Point, and Symantec are also DLPs that you should research into. You can search through these tools based off your needs and budget
#5. Educate Employees on Security Threats
Although your employees are your most trusted people in your business, they can pose an insider threat. According to IBM’s cyber security report, human error was the cause of 95% of all data breaches.
Having simple knowledge on recognizing and mitigating threats on the internet can reduce your chances of destroying your business. Teaching others about these threats can reduce your chances even more. Here are some basic data threats to know about, and how to prevent them:
Phishing:
-
-
Email, text, or call comes from someone who claims to be a high authority company
-
-
Can also masquerade as a fellow employee or loved one
-
-
Usually ask for personal information or credentials
-
-
Create a sense of urgency by notifying the user of a threat
-
-
Sometimes have poor grammar
-
-
Have suspicious links within the text or email.
Threats can masquarade as fellow colleagues. This is known as whaling.
How to spot phishing:
-
-
Hover over sender names in email addresses to check the actual email address
-
-
Check for grammar and misspellings
-
-
Check if the company can ask for personal information or credentials via website or by phone
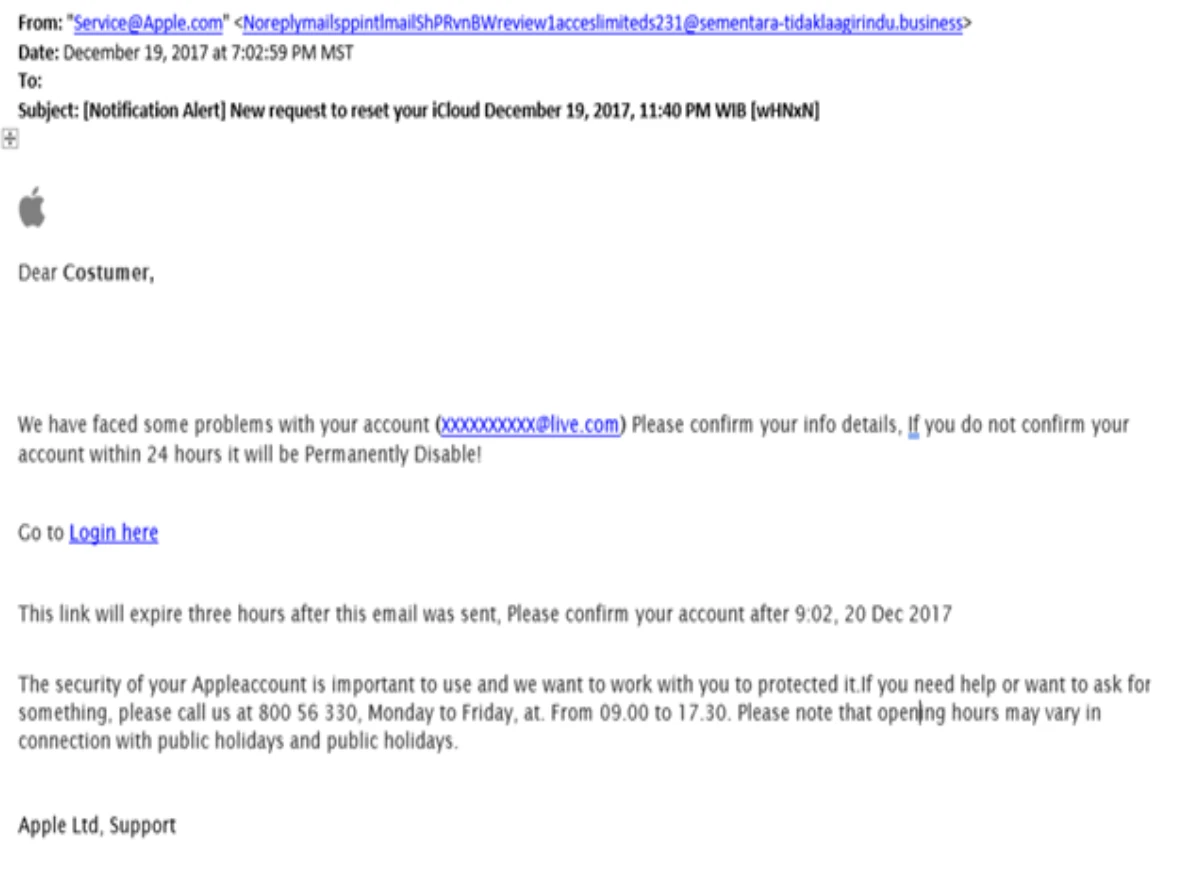
Phishing emails such as this one often pose as trusted companies such as Apple. Notice the suspicious link, urgent demand, and poor grammar?
Malicious Links and Malware:
-
-
Can appear in emails, social media posts, text messages, and seemingly trustworthy websites
-
-
Often offer a free download, content, or urgent demands
-
-
Have suspicious destination URLs
How to spot malicious links and malware:
-
-
Legitimate links typically won't contain misspellings or typos in the website domain name. Locate URLs with unorthodox characters and extensions such as .exe or .zip
-
-
Shortened links using services like Bitly can hide the true destination. Avoid clicking shortened URLs in emails or messages from unknown senders.
-
-
Make sure you hover your cursor over a link before clicking. Check if the URL at the bottom of the corner displays something different than what the link you are hovering around says.
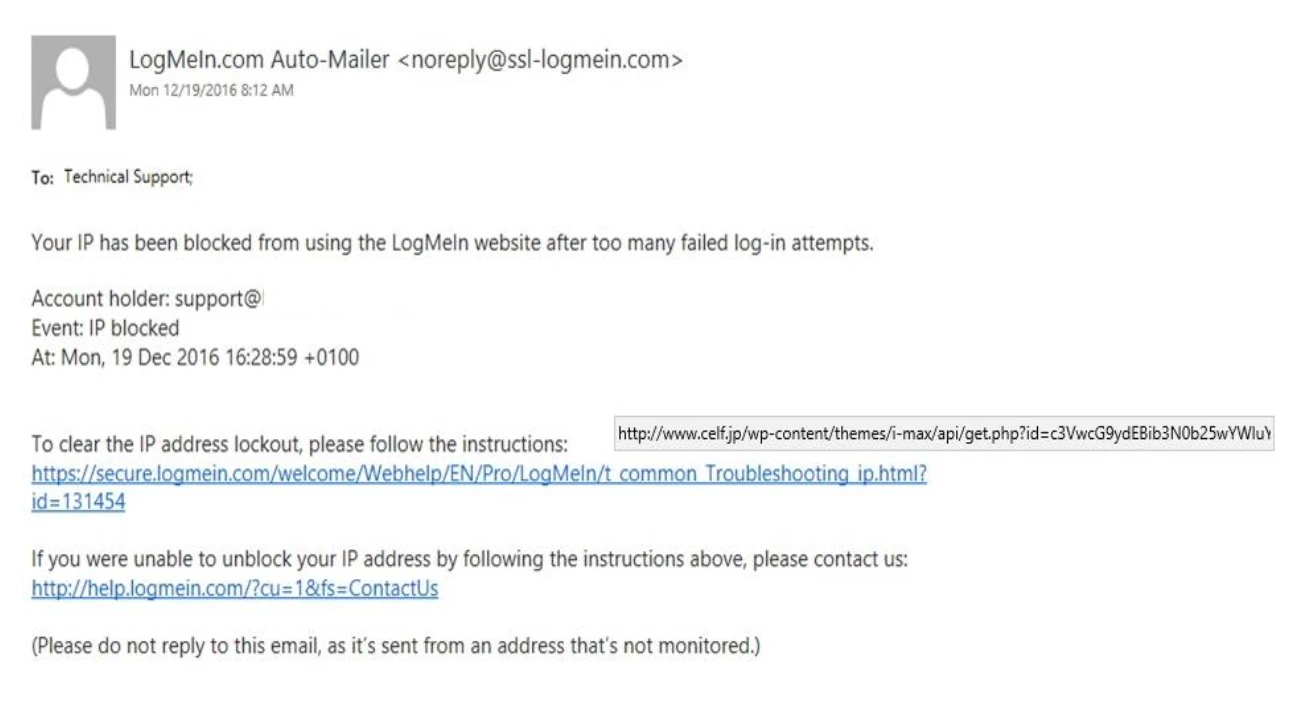
Make sure to hover over the link to check legitmacy. Suspicious links can be easily avoided if you pick up the habit of checking links.
Accidental Data Sharing:
-
-
Data can be leaked through email, the cloud, and USBs
-
-
Missending of emails to unauthorized recipients of data
-
-
Cloud permissions can make data accessible to anybody
-
-
File sharing can occur within prohibited third party platforms
How to Prevent Accidental Data Sharing
-
-
Enforce access controls that limit employee access to data based on their job roles. The principle of least privilege applies: give employees only the access they need to perform their tasks.
-
-
Make sure to encrypt sensitive data stored on servers and while being transferred
-
-
Configure the collaboration tools and cloud storage platforms with strict permission settings. Control who can view, edit, or share sensitive information.
-
-
Configure collaboration tools to prevent accidental sharing with the public by default.
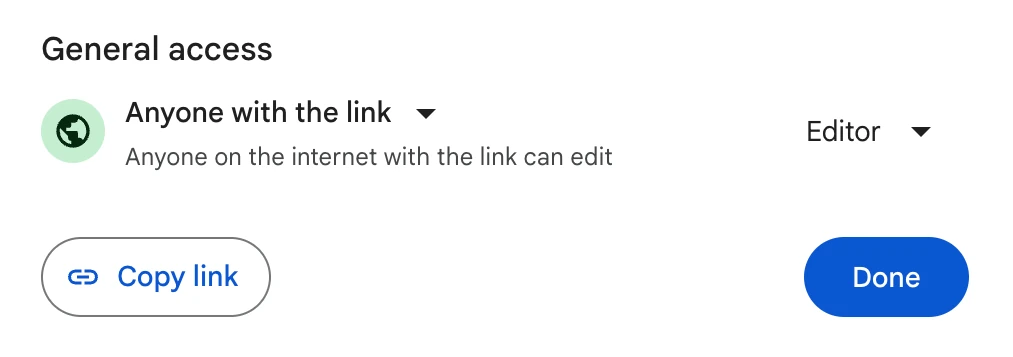
Even controlling view permissons in Google Docs can be easy ways to prevent data loss.
Errors in Physical Security:
-
-
Weak locks
-
-
Unsupervised entrances
-
-
Tailgating authorized personnel through entrances
-
-
Masquerading to personnel as an employee or someone of authority to gain access
-
-
Poor device tracking and accountability
How to prevent Errors in Physical Security:
-
-
Make sure your business has sturdy and industry recommended locks. If you are willing to, installing keypads and keycards are great ways to integrate security into your business.
-
-
Tell employees to be wary of those following them closely into entry points.
-
-
Keep accurate records of devices to detect potential theft.
How to Ensure You Have a Backup and Recovery Plan
At the end of the day, data loss prevention is only one part of the important battle to protect your business. Using these tips are useful, but your data will ultimately be safer by partnering up with an IT partner that suits your business needs. Without a plan or partner, disaster recovery would be difficult or even impossible.
At Strategica IT Solutions, we specialize in storing and recovering your data with industry recommended procedures. See how we can design a data storage and recovery plan that is just right for any business need and budget.