#4. Fortinet FortiGate
View the website
Features:
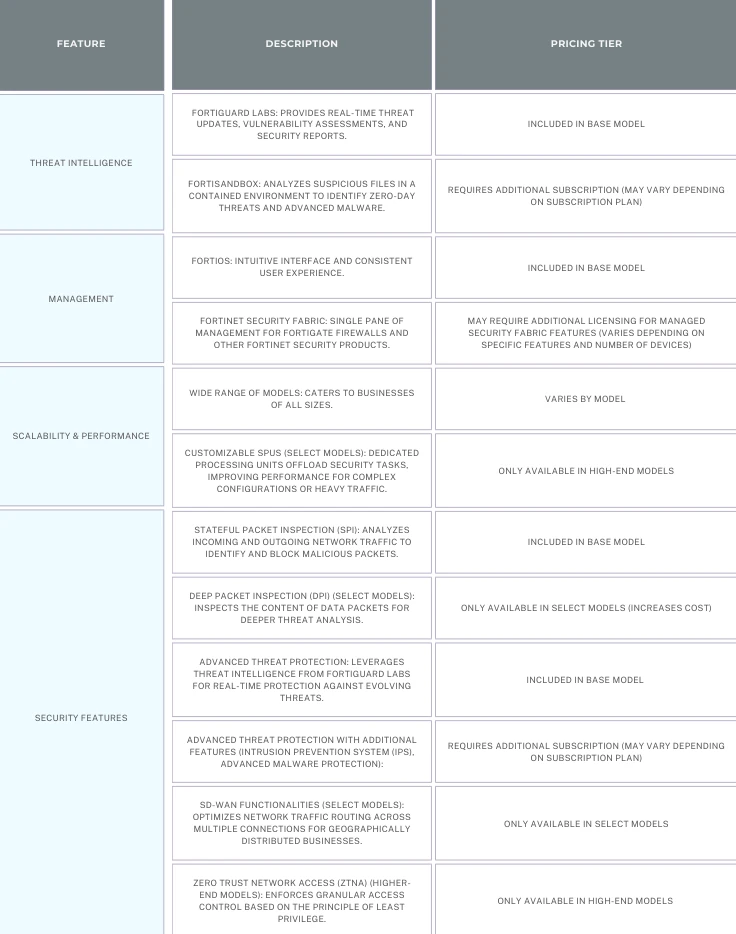
- FortiGuard Labs Threat Intelligence: Fortinet leverages its extensive FortiGuard Labs threat intelligence to provide comprehensive protection against evolving cyber threats. This includes real-time threat updates, vulnerability assessments, and security reports.
- FortiSandbox (Select Models): High-end FortiGate models offer integrated FortiSandbox sandboxing technology. This allows for dynamic analysis of suspicious files in a contained environment to identify zero-day threats and malware that might bypass traditional signature-based detection.
- Single Pane of Management: Fortinet Security Fabric delivers a single pane of management for not only FortiGate firewalls but also other Fortinet security products like intrusion prevention systems (IPS) and access points. This simplifies security management for organizations with a Fortinet security ecosystem.
- FortiAP Integration (Select Models): Select FortiGate models offer native integration with Fortinet access points (FortiAPs). This enables features like automatic policy deployment, centralized threat management, and guest Wi-Fi access control through a unified interface.
Pros:
-
Scalability and Performance:
- Wide Range of Models: Fortinet offers a comprehensive selection of FortiGate firewalls catering to businesses of all sizes. This ranges from entry-level models like the FortiGate 40F, suitable for small businesses, to high-end models like the FortiGate 3200F, designed for large enterprises with demanding network requirements.
- Customizable Security Processing Units (SPUs): Higher-end FortiGate models utilize custom-designed SPUs. These SPUs offload security tasks like encryption and decryption from the main CPU, freeing up resources for other critical operations. This translates to significantly improved overall firewall performance, especially when handling heavy network traffic or complex security configurations.
- Flexible Deployment Options: FortiGate firewalls can be deployed in various configurations. They can function as standalone firewalls, be clustered for high availability and redundancy, or integrated into a larger security fabric alongside other Fortinet security products.
-
Advanced Security Features:
- Deep Packet Inspection (DPI) (Select Models): While basic models offer stateful packet inspection (SPI), higher-end FortiGate firewalls feature DPI capabilities. DPI goes beyond analyzing packet addresses by inspecting the content of data packets. This allows for deeper inspection of application protocols and data payloads to identify sophisticated threats that might evade traditional signature-based detection.
- Advanced Threat Protection: FortiGate firewalls leverage threat intelligence from Fortinet FortiGuard Labs. This real-time intelligence provides protection against evolving cyber threats, including zero-day attacks, malware variants, and emerging exploits.
- SD-WAN (Software-Defined Wide Area Network) Capabilities (Select Models): Certain FortiGate models offer built-in SD-WAN functionalities. This allows businesses with geographically distributed locations to intelligently route internet traffic across multiple connections for improved performance, reliability, and cost-efficiency.
- Zero Trust Network Access (ZTNA) (Higher-End Models): Select FortiGate models provide Zero Trust Network Access (ZTNA) functionalities. ZTNA enforces the principle of "least privilege," granting access to resources only to authorized users and devices, regardless of their location.
-
Simplified Management and Centralized Control:
- FortiOS: FortiGate firewalls utilize Fortinet's security-focused operating system, FortiOS. FortiOS is known for its intuitive interface and consistent user experience across the entire FortiGate product line. This simplifies security management for organizations with diverse FortiGate deployments. Additionally, FortiOS offers features like:
- Federated Management: Allows for centralized configuration and policy management of multiple FortiGate firewalls across a distributed network.
- Automated Threat Detection and Response: Streamlines the process of identifying, investigating, and containing security incidents.
- Integration with Fortinet Security Fabric: FortiGate firewalls integrate seamlessly with other Fortinet security products like intrusion prevention systems (IPS) and access points. This unified security fabric offers a centralized management console for all your Fortinet security solutions.
Cons:
- Management Complexity (High-End Models): Advanced features on high-end models might require more technical expertise to manage effectively.
- Pricing Complexity: With a vast range of models, pricing can vary significantly.
Pricing:
- Specific pricing information for Fortinet FortiGate firewalls is not publicly available due to the vast range of models, but here’s what we found on retailer websites:
- Lower-end models (FortiGate 40F, 60E): $392.05 - $1,261.00 These models are suitable for small businesses or branch offices.
- Mid-range models (FortiGate 80F, 100F): $1,915.49 - $2,211.30 These models offer more performance and features for medium-sized businesses.
- High-end models (FortiGate 300F, 400F): Pricing is not readily available online for these high-end models designed for large enterprises. You'll need to contact Fortinet or an authorized reseller for a quote.
- Contact Fortinet or an authorized reseller for quotes tailored to your specific needs. Consider factors like the number of users, required features, and desired level of performance when requesting a quote.
You Should Consider Fortinet FortiGate If:
- You need a wide range of features and performance options: Fortinet offers a comprehensive line of FortiGate models catering to various needs.
- Advanced security features are a priority: FortiGate firewalls are known for their robust security features, including intrusion prevention, application control, deep packet inspection, and threat intelligence integration. They are a strong choice for organizations that require comprehensive security protection.
- Centralized management is important: Fortinet offers FortiGate Management Center, a centralized platform for managing and monitoring multiple FortiGate devices across your network.
#5. Palo Alto Networks PA-Series
View the website
Features:
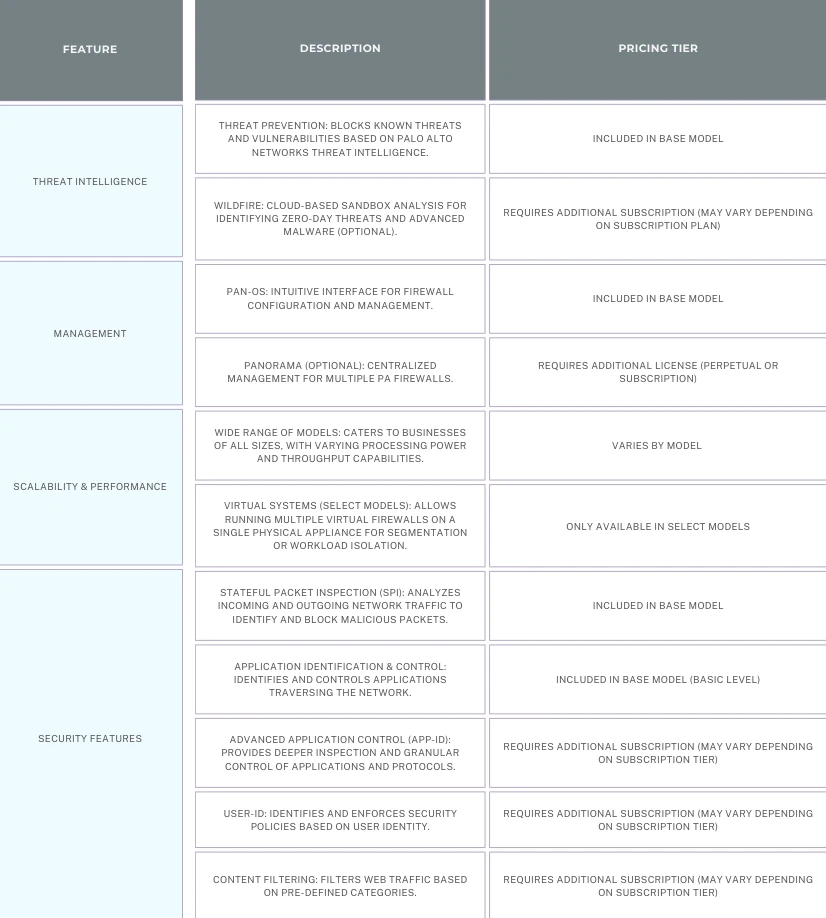
- App-ID: Identifies and classifies all applications traversing the network, regardless of port or protocol. This allows for granular control over application traffic and helps enforce security policies.
- User-ID: Identifies individual users on the network, enabling security policies to be applied based on user identity, not just IP address.
- GlobalProtect: Offers a secure remote access solution that allows users to connect to the corporate network securely from any device.
- Panorama (Optional): Provides a central management console for simplified management of multiple PA Series firewalls across geographically distributed locations.
Pros:
-
Advanced Threat Prevention:
- Next-Generation Firewall (NGFW) Functionality: The PA Series goes beyond traditional firewalls by offering deep packet inspection (DPI) to identify and block malware, exploits, and other threats hidden within application traffic.
- Sandboxing (Optional): Advanced models offer optional sandboxing capabilities that isolate suspicious code for detonation in a safe environment.
- Threat Prevention Updates: Palo Alto Networks is known for its frequent threat intelligence updates so you stay current with the latest security threats.
-
Scalability and Performance:
- Wide Range of Models: The PA Series offers a variety of models catering to businesses of all sizes, from small offices to large enterprises.
- High-Performance Processing: PA Series firewalls are known for their powerful processors, enabling them to handle heavy network traffic volumes and complex security configurations without compromising performance.
-
Simplified Management (Optional):
- Panorama (Centralized Management): While the web interface offers individual firewall management, the optional Panorama console provides centralized management of multiple PA Series firewalls.
- Automation Features: The PA Series offers automation features that can streamline tasks like security policy creation and deployment, reducing administrative workload.
Cons:
- Complexity: Palo Alto firewalls can be complex to set up and manage, requiring skilled IT professionals.
- Cost: PA-Series firewalls are generally more expensive compared to some competitors.
Pricing:
- Specific pricing information for Palo Alto Networks PA-Series firewalls is not publicly available. Due to their high performance and advanced features, they tend to be on the more expensive side, usually ranging in the thousands ($1,000-$10,000) for small businesses.
- Contact Palo Alto Networks or an authorized reseller for quotes tailored to your specific needs.
Who Should Consider Palo Alto PA-Series:
- Next-generation security features are crucial: The PA Series is known for its advanced NGFW capabilities, including application identification and control, intrusion prevention, URL filtering, and advanced threat protection. This makes them a strong choice for organizations facing sophisticated cyber threats.
- Scalability and performance are essential: The PA Series offers a wide range of models with varying processing power and throughput capabilities.
- Centralized management is a priority: Panorama offers a way to configure, monitor, and report across your entire PA Series deployment.
#6. Sophos XG Firewall
View the website
Features:
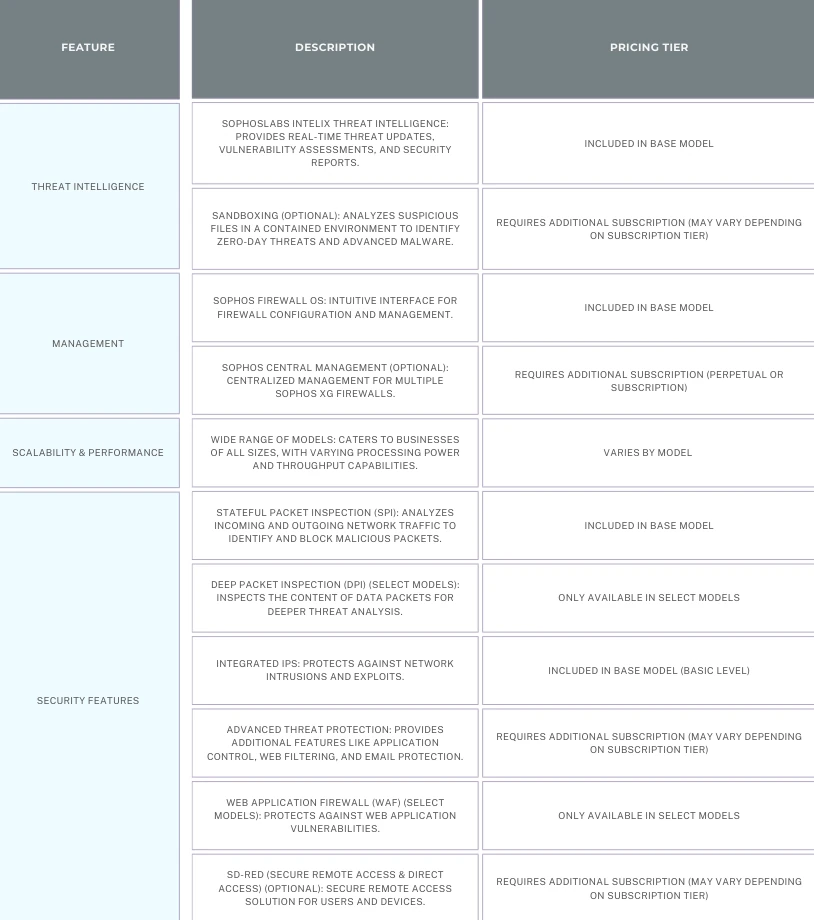
- Synchronized Security: Sophos XG Firewall integrates with other Sophos security products like endpoint protection and email security. This enables features like Sophos Synchronized Threat Response, which automatically shares threat intelligence across Sophos products to improve overall security posture.
- DeepGuard Sandbox Analysis (Plus Models): Sophos XG Firewall offers optional DeepGuard sandboxing technology in Plus models. Similar to other sandboxing solutions, this allows for dynamic analysis of suspicious files to identify zero-day threats.
- Web Application Firewall (WAF) Functionality (Plus Models): Plus models also offer built-in WAF capabilities to protect web applications from common attacks like SQL injection and cross-site scripting (XSS).
- Flexible Management: Sophos XG Firewall offers multiple management options, including a user-friendly web interface, on-premise Sophos Central management console, or cloud-based Sophos Central cloud management. This caters to businesses with varying preferences for managing their security infrastructure.
Pros:
-
Best-in-Class Threat Prevention:
- SophosLabs Global Threat Network: Sophos leverages its extensive network of security researchers to stay ahead of emerging threats, blocking zero-day attacks and malware variants.
- Sandboxing (Plus Models): Suspicious files are isolated in a safe environment to observe their behavior and identify advanced malware that might slip through traditional defenses.
-
High Performance:
- Dedicated Hardware: Sophos XG Firewall utilizes specialized components to handle demanding network traffic efficiently, ensuring smooth operation even for large organizations.
- Traffic Optimization: The firewall prioritizes business-critical applications, minimizing delays for crucial operations.
- Fast Processing: Sophos optimizes specific network traffic types for faster data transfer.
-
Scalability:
- Range of Models: Choose a firewall that meets your current needs, with the ability to upgrade to a more powerful model as your business grows.
- Centralized Management: Sophos Central simplifies managing multiple firewalls across different locations from a single cloud-based platform.
Cons:
- Limited Logging and Reporting (For Some): While basic logging is available, some users find the reporting capabilities less comprehensive compared to other NGFW solutions. This might be a limitation for businesses requiring detailed security audits or forensic analysis.
- Steeper Learning Curve (For Some): While generally considered user-friendly, Sophos XG Firewall offers a wider range of advanced features compared to the WatchGuard T Series. This may require a slightly steeper learning curve for less technical users.
- Limited Free Version Capabilities: The free XG Firewall Home Edition offers a limited feature set compared to the paid versions. Upgrading to a paid license is necessary to unlock essential functionalities for business use.
Pricing:
- Specific pricing information for Sophos XG Firewall is not publicly available due to the subscription-based model and variations depending on features and needs. However, here's a general idea based on retailer examples and Sophos' offerings:
- Subscription Model: Sophos offers a subscription-based licensing model, typically involving an annual or multi-year upfront cost that covers software updates, threat intelligence feeds, and technical support.
- Hardware Costs: Retailer websites list hardware appliances like Sophos XG 125 Rev.2 for around $349.99 (USD) and Sophos XGS 3300 for $14,713.99 (USD).
- Expectation: Expect the total cost to be higher than just the hardware price, as the subscription is essential for full functionality.
- Here's how to get an accurate quote:
- Sophos Website: The Sophos website likely offers a quote request form or contact information for their sales team. They can provide the most up-to-date pricing based on your specific needs (model, features, subscription length). https://www.sophos.com/en-us
- Retailer Websites: Many retailers like CDW or Insight might have online quote request forms or allow you to contact their sales representatives for a customized quote based on your chosen hardware and subscription options.
You Should Consider Sophos XG Firewall If:
- You Have Limited IT Resources:
- User-friendly interface and central management (Sophos Central) make it manageable for SMBs with limited IT resources.
- Scalability of models ensures it can grow alongside your business needs.
- You Require Centralized Management:
- Sophos Central allows for centralized management of multiple XG Firewalls from a single console, simplifying administration for businesses with geographically distributed locations.
- You Need a Balance of Features and Usability:
- While not as feature-rich as high-end solutions, Sophos XG Firewall offers a comprehensive feature set (application control, IPS, web filtering) at a competitive price point. This is ideal for businesses seeking a balance between robust security and ease of management.
#7. Cisco Secure Firewall
View the website
Features:
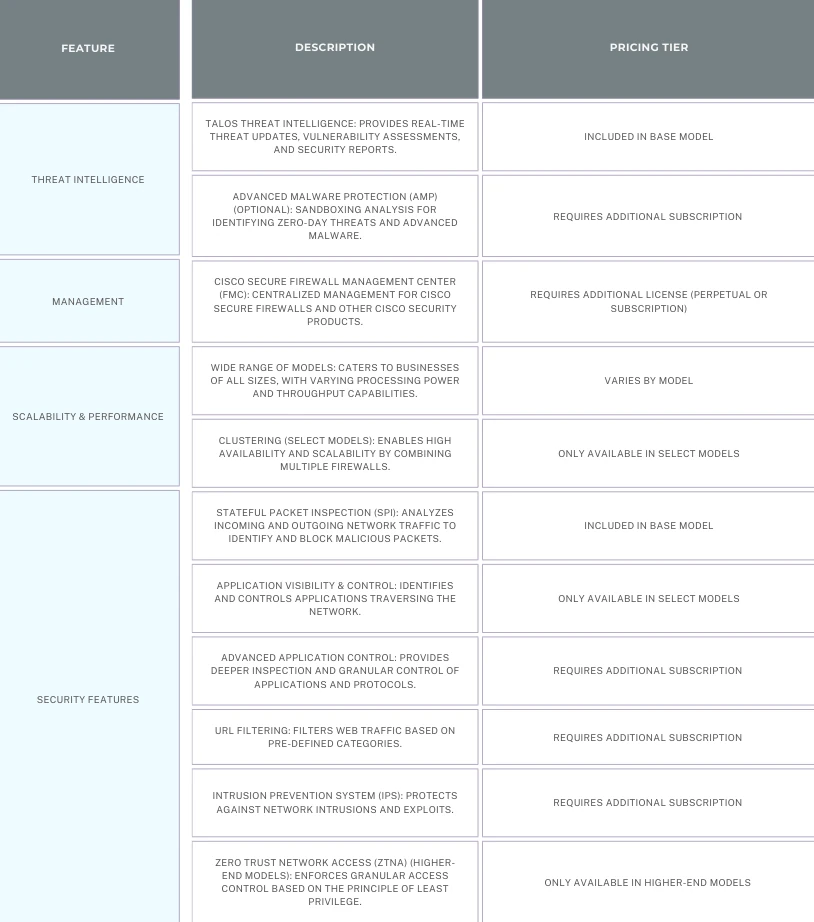
- Next-Generation Intrusion Prevention System (NGIPS):
- Signature-Based Detection: Identifies known threats by matching network traffic patterns to a database of malicious signatures.
- Anomaly Detection: Analyzes network traffic patterns for unusual behavior that might indicate a new or unknown threat.
- Deep Packet Inspection (DPI) (Optional): Examines the actual content of data packets to identify malicious payloads hidden within seemingly legitimate traffic.
- Sandboxing (Select Models)
- Application Visibility and Control (AVC):
- Application Identification: Secure Firewall identifies all applications using your network, including business-critical applications, social media platforms, and productivity tools.
- Policy Enforcement: You can define policies for each application. For example, prioritize bandwidth for critical video conferencing applications while restricting access to social media during work hours.
- User-Based Control: (With User ID Integration) AVC can be combined with User ID integration to enforce application access controls based on specific users or user groups. This allows you to restrict access to sensitive applications based on user identity.
- URL Filtering:
- Threat Intelligence Feeds: Secure Firewall leverages threat intelligence feeds to identify malicious websites known for phishing attacks, malware distribution, or other harmful activities.
- Category-Based Blocking: You can block access to entire categories of websites, such as gambling sites or social media platforms.
- Custom URL Blocking: Additionally, you can create custom lists of websites to be blocked based on your specific security needs.
Pros:
-
Reliable and High-Performance:
- Hardware Acceleration: Dedicated hardware components like cryptographic accelerators take the heavy lifting out of security tasks like encryption and decryption.
- Scalability and Performance Optimization: Cisco offers a range of Secure Firewall models with varying processing power and capabilities. Optimized Software: Cisco Secure Firewall is built on a foundation of optimized software that efficiently utilizes hardware resources. This means smooth performance without sacrificing security effectiveness.
-
Scalable Architecture:
- Modular Design: Cisco Secure Firewall utilizes a modular design, allowing you to add additional features and processing power as your network grows and your security needs evolve.
- Centralized Management: Even with multiple Secure Firewalls deployed across your network, you can manage them centrally from a single console. This simplifies security management and reduces the risk of configuration errors.
- Cloud-Based Management Option: (Depending on deployment model) For some Secure Firewall models, cloud-based management is available. This eliminates the need for on-premise management infrastructure and allows for easy remote access and configuration changes.
-
Advanced NGFW Features:
- Multi-Layered Threat Protection: Cisco Secure Firewall goes beyond basic firewalls by offering a comprehensive suite of NGFW features. This layered approach provides robust defense against a wide range of threats, including malware variants, zero-day attacks, application exploits, and malicious websites.
- Advanced Threat Detection: Features like Sandboxing (on select models) and Deep Packet Inspection (optional) are present.
- Integration with Threat Intelligence Feeds: Secure Firewall leverages threat intelligence feeds to stay up-to-date on the latest threats and malicious activities.
-
High Availability Clustering:
- Business Continuity: In mission-critical environments, even a brief firewall outage can be disastrous. High availability clustering ensures continuous operation and minimizes downtime.
- Automatic Failover: If a single firewall in the cluster experiences an outage, the remaining firewalls automatically take over the security duties, ensuring seamless network protection. This eliminates the risk of a security gap during firewall maintenance or unexpected hardware failures.
- Scalability and Redundancy: You can add additional firewalls to the cluster for increased redundancy and scalability. This allows you to adapt your security posture to changing network demands and ensure maximum uptime.
Cons:
- Cost: Can be more expensive compared to some competitors.
- Complexity: Managing advanced features might require specialized IT skills.
Pricing:
- Cisco Secure Firewall pricing is not publicly available. Here's what you can expect:
- Contact Cisco: Since pricing varies depending on the specific model, features, and configuration, contacting Cisco or a certified reseller is necessary for a quote.
- Scalability Affects Cost: The cost will scale based on the features and processing power required for your network size and security needs.
Choosing Cisco Secure Firewall:
- Ideal for businesses that prioritize robust security and have the resources to manage it. This includes organizations in:
- Highly regulated industries
- Sensitive data handling
- High risk of cyberattacks
- If budget is a major concern and your IT resources are limited, consider exploring alternative NGFW solutions that might offer a better fit.
#8. Checkpoint Next Generation Firewall
View the website
Features:
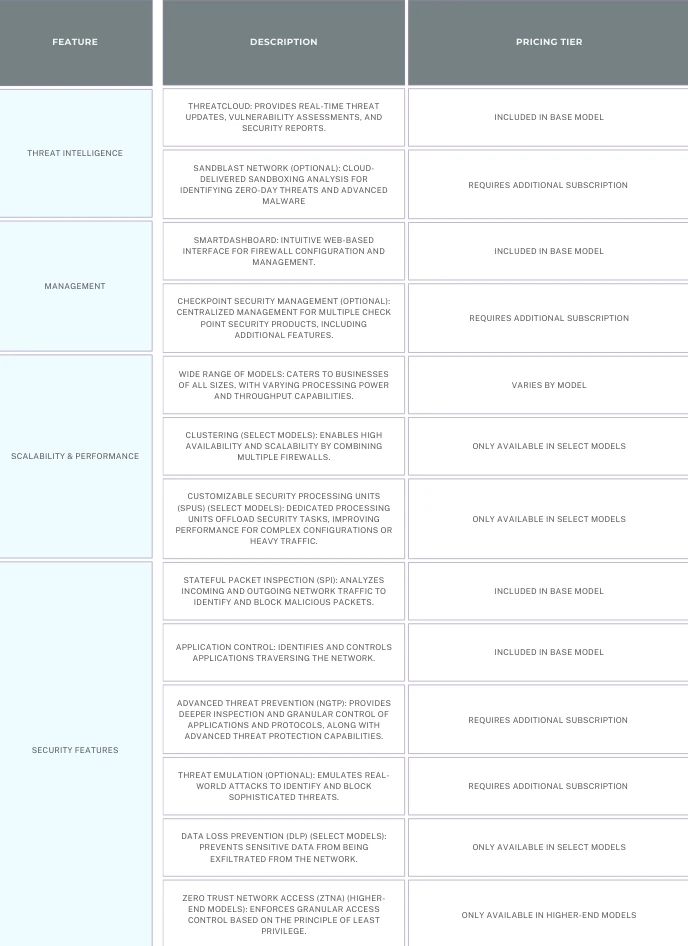
- Next-Generation Intrusion Prevention System (NGIPS): Similar to Cisco Secure Firewall, Checkpoint NGIPS offers multi-layered protection:
- Signature-based detection: Identifies known threats using a database of malicious signatures.
- Threat Emulation: Goes beyond traditional signatures by simulating real-world attack scenarios to identify and block even previously unknown threats.
- Sandboxing (Select Models)
- Anomaly Detection: Analyzes network traffic patterns for unusual behavior that might indicate a new or unknown threat.
- Advanced Threat Prevention: Checkpoint NGFW boasts additional features for enhanced security:
- Threat Extraction: Sandboxing can go a step further by automatically extracting malicious payloads from infected files, rendering them harmless.
- Threat Hunting: Proactively searches for indicators of compromise (IOCs) within the network to identify and eliminate existing threats that might have bypassed initial defenses. Think of a security team actively searching for and eliminating hidden threats within the network.
- Identity Awareness: Integrates with user directory services to enforce security policies based on user identity and device type. This allows for more control over access permissions.
- Application Control: Checkpoint NGFW offers comprehensive application control functionalities:
- Application Identification: Similar to Cisco Secure Firewall, it identifies all applications traversing the network.
- Deep Packet Inspection (DPI)
- Granular Policy Enforcement: Define and enforce granular policies for each application, including bandwidth allocation, access control, and content filtering.
- Additional Features:
- URL Filtering, Mobile Security, and Integrated Threat Management (UTM) (on select models)
Pros:
-
High Performance: Check Point NGFWs are known for their ability to deliver high throughput and low latency, even with advanced security features enabled. This is important for organizations that require maximum network performance.
-
Sandblast Network Threat Prevention: This advanced sandboxing technology goes beyond traditional signature-based detection to identify and block zero-day attacks and other sophisticated threats.
-
Cloud-Delivered Security: Check Point offers a cloud-delivered security option that allows organizations to benefit from advanced threat prevention without the need for additional hardware or software.
-
Extensive Management Tools: Check Point offers a variety of management tools that make it easy to configure, monitor, and troubleshoot your NGFW. This includes a single pane of glass management console and powerful automation capabilities.
-
Integration with Security Fabric: Check Point NGFWs integrate seamlessly with Check Point's Security Fabric, a unified security architecture that provides comprehensive protection across your entire network.
Cons:
- Complexity: Similar to Cisco Secure Firewall, managing advanced features might require specialized IT skills.
- Potential Performance Impact: Deep Packet Inspection (DPI) and other advanced features can consume processing power, potentially impacting network performance on lower-end hardware.
Pricing:
- Checkpoint NGFW pricing is not publicly available and likely varies based on the specific model, features, and configuration. Here's a general expectation:
- Contact Checkpoint: Similar to Cisco, contacting Checkpoint or a certified reseller is necessary for a quote.
- You Should Consider Checkpoint NGFW If:
- Advanced Threat Prevention is a top priority.
- You require granular control over user and device access.
- Mobile security is a major concern for your organization.
- You're looking for a potentially unified UTM solution (on select models).
#9. Cisco Meraki MX
View the website
Features:
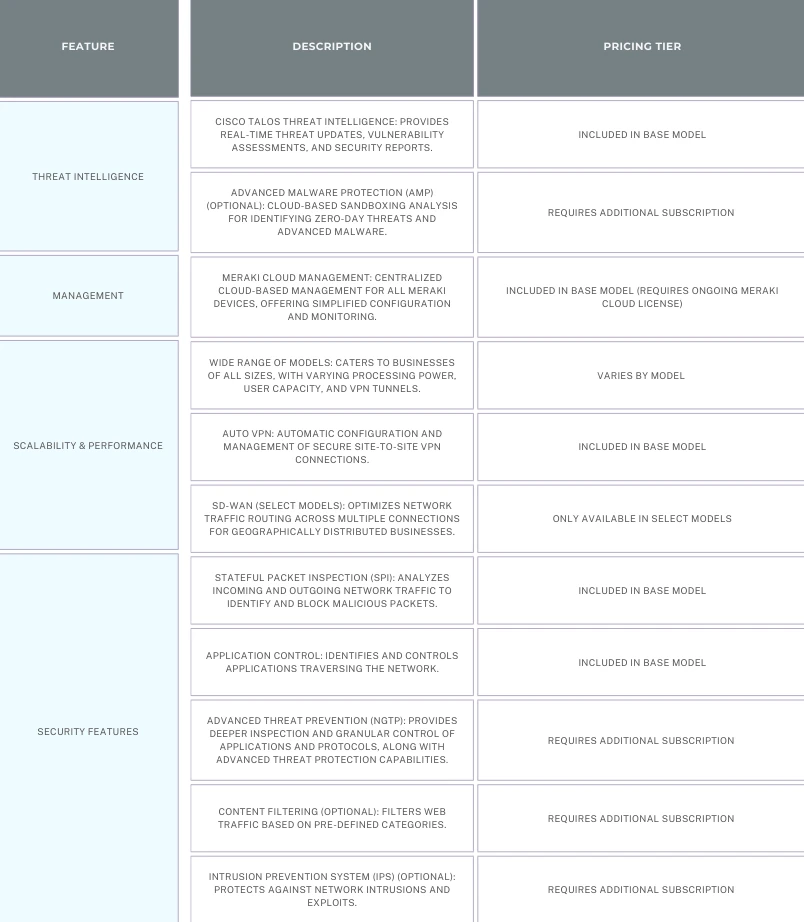
- Next-Generation Intrusion Prevention System (NGIPS): Provides multi-layered protection against a wide range of threats, including malware, exploits, and unauthorized access attempts. This includes:
- Signature-based detection
- Anomaly detection (on some models)
- Optional Deep Packet Inspection (DPI) for deeper traffic analysis
- Application Control: Offers control over applications traversing your network. You can identify all applications, prioritize business-critical ones (like video conferencing), and restrict access to less essential applications (like social media) during work hours.
- URL Filtering
- Content Filtering: (on some models) Provides advanced content filtering capabilities to restrict access to specific types of content, such as gambling or adult websites.
- VPN (Virtual Private Network): Enables secure remote access to your network for employees and authorized users. Meraki MX offers features like AutoVPN for effortless site-to-site VPN connections.
- SD-WAN (Software-Defined Wide Area Network): (on some models) Provides intelligent traffic routing and bandwidth optimization across multiple internet connections, improving network performance and redundancy.
- Cloud-Based Management: A key differentiator. Meraki MX is entirely managed from a centralized cloud dashboard. This simplifies configuration, deployment, and ongoing monitoring, eliminating the need for on-premise management infrastructure.
Pros:
- Ease of Use: Cloud-based management makes Meraki MX ideal for organizations with limited IT resources or geographically dispersed networks.
- Scalability: Meraki offers a range of MX models with varying processing power and capabilities.
- Centralized Visibility and Control: The cloud dashboard provides a centralized view of your entire network security posture. You can easily monitor traffic, configure policies, and troubleshoot issues from a single location.
- Automatic Updates: Meraki MX receives automatic firmware and security updates.
- Integration with Other Cisco Meraki Products: Meraki MX integrates seamlessly with other Meraki products, such as access points and switches, for a unified network management experience. (if applicable)
Cons:
- Vendor Lock-In: Meraki MX relies on the Cisco Meraki cloud platform for management and updates. Switching vendors would require replacing your entire firewall infrastructure.
- Limited Customization: While offering essential NGFW features, Meraki MX might not provide the same level of control and customization options as some competitor solutions.
- Potential Performance Impact: Cloud-based management can introduce latency, potentially impacting performance on geographically dispersed networks. (consider bandwidth limitations)
- Subscription Model or Licensing Costs: Pricing might be based on a subscription model or upfront licensing costs depending on the chosen model and features.
Pricing:
- Here's what we found on retailer websites (pricing may vary):
- Meraki MX64: $295.00 - $463.28
- Meraki MX67: $309.87 - $411.06
- Meraki MX84: $1,995.45
- Meraki MX100: $399.99 - $745.00
- Meraki MX250: $9,995.00
- Meraki MX450: $19,995.00
- You Should Consider Meraki MX If:
- Ease of use and cloud-based management are priorities.
- You have a growing network and require a scalable solution.
- You value centralized visibility and control over your network security.
- You already use other Cisco Meraki products and desire a unified network management experience.
#9. Barracuda CloudGen Firewall
View the website
Features:
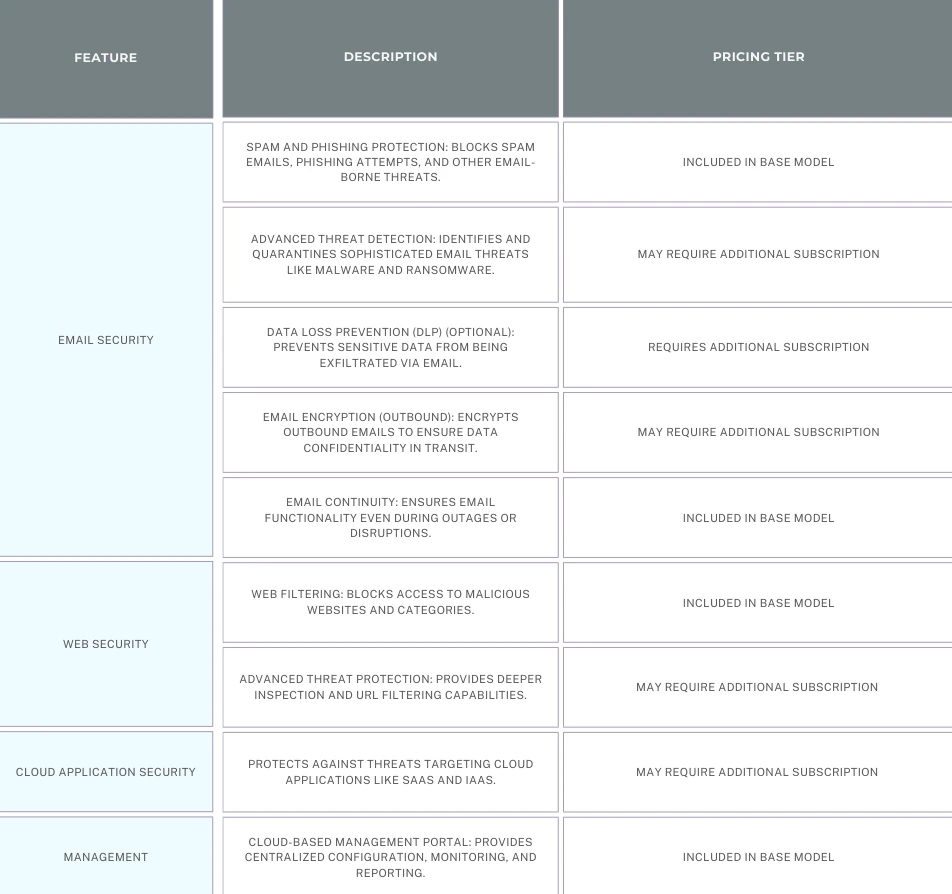
- Web Application Firewall (WAF): The heart of BCGF, the WAF blocks malicious traffic targeting your web applications. It employs various techniques like:
- Signature-Based Detection: Identifies and blocks known attack patterns based on a continuously updated threat intelligence database.
- Negative Security Model (Blacklisting): Blocks traffic matching predefined malicious patterns.
- Positive Security Model (Whitelisting): Only allows traffic that adheres to pre-defined safe behavior patterns, offering a stricter security stance.
- Anomaly Detection: Detects and blocks suspicious traffic patterns that deviate from normal user behavior.
- DDoS Mitigation: Protects your web applications from Distributed Denial-of-Service (DDoS) attacks that can overload your servers with a flood of traffic, rendering them inaccessible to legitimate users. BCSS employs techniques like traffic filtering, rate limiting, and challenge-response mechanisms to mitigate DDoS attacks.
- API Security: Many modern web applications rely on APIs to connect with other systems or services. BCGF safeguards these APIs by protecting against common API vulnerabilities like unauthorized access, data breaches, and injection attacks.
- Bot Management: Malicious bots can scrape data, launch attacks, or engage in fraudulent activity. BCGF helps identify and block these bots using techniques like behavior analysis and threat intelligence.
- Advanced Bot Detection: BCGF goes beyond basic bot blocking by offering advanced features like user behavior analysis and browser fingerprinting to distinguish between legitimate users and sophisticated bots that mimic human behavior.
- Reputation Filtering: Leverages threat intelligence to block traffic originating from known malicious IP addresses or sources associated with bot activity or cyberattacks.
- Customizable Security Policies: Granular control allows you to tailor security policies specific to your web applications and risk tolerance.
- Reporting and Analytics: BCGF provides detailed reports and analytics on web traffic, security events, and blocked attacks. This data helps you gain insights into potential security threats and identify areas for improvement in your security posture.
Pros:
- Focused Expertise: Unlike NGFWs with broader network security features, BCGF specializes in web application security, offering a comprehensive suite of tools specifically designed to protect web applications.
- Enhanced Security: The combined protection of WAF, DDoS mitigation, API security, and bot management creates a robust defense against various web-based threats.
- Improved User Experience: By blocking malicious traffic and DDoS attacks, BCGF ensures a smooth user experience for legitimate visitors to your web applications.
- Reduced IT Burden: Cloud-based deployment simplifies management and ongoing maintenance compared to on-premise web application security solutions. Automatic updates ensure consistent protection against evolving threats.
- Scalability: BCGF scales effortlessly to accommodate growth in web traffic and complexity of your web applications.
Cons:
- Complexity: CloudGen Firewall's extensive feature set can make setup and management more complex compared to user-friendly firewalls. In-house expertise or Barracuda support might be required for advanced configurations.
- Potential Cost: Due to customizable features and potential enterprise focus, CloudGen Firewall might be more expensive than basic cloud-delivered firewalls. Consider your budget constraints.
- Vendor Lock-In: Tight integration with Barracuda Networks' security ecosystem could necessitate significant security architecture changes if switching to a different vendor in the future.
Pricing:
- Pricing: Barracuda does not publicly advertise specific pricing for BCGF. Here's what to expect:
- Contact Barracuda Networks or a Reseller: Due to the various configuration options and potential volume discounts, contacting Barracuda or a certified reseller is necessary for an accurate quote.
- Subscription Model: BCGF is offered as a subscription service with different tiers based on features, protected web applications, and bandwidth requirements.
- Custom Considerations: The cost will depend on the number of web applications you need to protect, the chosen security features (e.g., advanced bot detection), and the amount of web traffic you experience.
Consider BCGF if you are:
- A small business with a primary focus on web application security and limited resources or expertise to manage complex security solutions.
- A business that relies heavily on web applications for your core operations and requires robust protection against web-based threats.
- An organization already using Barracuda security products seeking a complementary layer of web application security.
- E-commerce businesses handling sensitive customer data and financial transactions that require enhanced security measures.
#11. Palo Alto Prisma Cloud NGFW
View the website
Features:
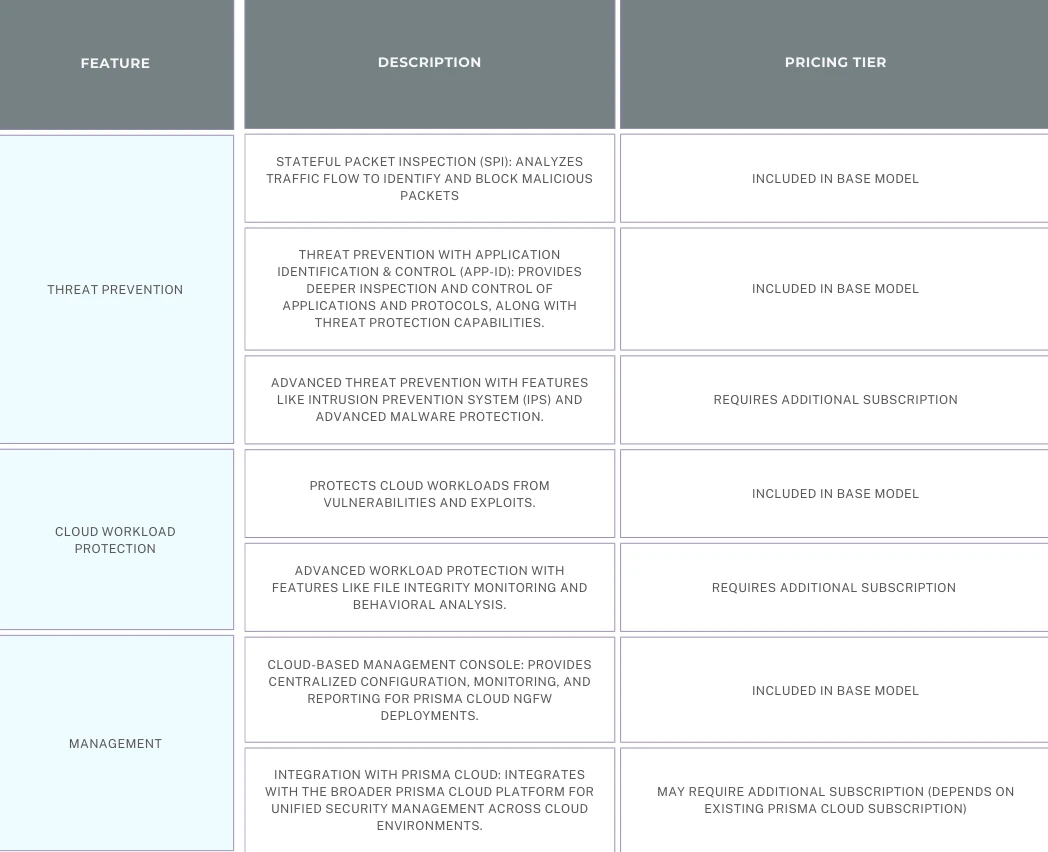
- Next-Generation Intrusion Prevention System (NGIPS): Provides multi-layered protection against known and unknown threats, including malware, exploits, and zero-day attacks. This includes:
- Signature-based detection
- Advanced Threat Prevention (like sandboxing on select models)
- Deep Packet Inspection (DPI)
- Application Control: Offers granular control over applications traversing your cloud workloads. You can identify applications, prioritize business-critical ones, and enforce security policies to restrict access to unauthorized or risky applications.
- Cloud Workload Protection Platform (CWPP): Prisma Cloud goes beyond NGFW functionalities by offering a broader CWPP platform. This includes features like vulnerability management, workload firewalling, and container security to secure your entire cloud environment.
- User and Entity Behavior Analytics (UEBA): Analyzes user and entity behavior within your cloud environment to identify potential insider threats or anomalous activity.
- Cloud-Native Security: Designed specifically to secure cloud environments. Prisma Cloud integrates seamlessly with major cloud platforms like AWS, Azure, and GCP, leveraging their native security features and functionalities.
- Cloud-Based Management: Similar to other cloud-delivered NGFW solutions, Prisma Cloud is entirely managed from a centralized cloud dashboard. This simplifies configuration, deployment, and ongoing monitoring across your multi-cloud environment.
- Automatic Updates: Ensures your cloud security posture remains up-to-date with the latest threat intelligence and security patches.
Pros:
- Comprehensive Security: Provides advanced NGFW features alongside broader CWPP functionalities for holistic cloud security.
- Cloud-Native Integration: Integrates seamlessly with major cloud platforms, leveraging their native security features for optimal protection.
- Scalability: Easily scales to accommodate growing cloud workloads and evolving security needs.
- Centralized Management: Simplifies security management across your entire multi-cloud environment.
- Continuous Threat Detection: Advanced threat prevention and UEBA capabilities help identify and mitigate sophisticated cyberattacks.
Cons:
- Complexity: Implementing and managing a comprehensive cloud security platform like Prisma Cloud might require specialized expertise.
- Potential Cost: Due to its advanced features and enterprise focus, Prisma Cloud might be more expensive compared to basic cloud-delivered NGFW solutions.
- Vendor Lock-In: Prisma Cloud integrates tightly with Palo Alto Networks security ecosystem. Switching to another vendor might require significant security architecture changes.
Pricing:
- Pricing: Palo Alto Networks does not publicly advertise specific pricing for Prisma Cloud. Here's what to expect:
- Contact Palo Alto Networks or a Reseller: Due to the customizable nature of cloud security solutions and potential enterprise discounts, contacting Palo Alto Networks or a certified reseller is necessary for a tailored quote.
- Subscription Model: Prisma Cloud is offered as a subscription service with various tiers based on features, protected workloads, and user licenses.
- Custom Quote: The cost will depend on your specific cloud environment size, security needs, and desired features within the Prisma Cloud platform.
- You Should Consider Prisma Cloud If:
- Comprehensive cloud security with NGFW functionalities and broader CWPP features is a priority.
- You have a complex multi-cloud environment and require a unified security platform.
- You value advanced threat prevention capabilities and threat intelligence.
- You have the resources and expertise to manage a comprehensive cloud security solution.
Frequently Asked Questions
Here are some of the most frequently asked questions surrounding the process of choosing and setting up a next gen firewall:
Q. How do I set up a firewall for my small business?
A. Planning is key! Identify your valuable data and network layout. Choose a user-friendly firewall (e.g., Untangle NG Firewall, WatchGuard T Series) that scales with your business and consider hardware or cloud-based deployment based on your needs. But if you’re talking about deployment and configuration, here’s an overview of what to expect:
-
1. Hardware Setup (if applicable): Physically install the firewall appliance at your internet gateway (your connection to the web) and connect it to your network devices.
-
2. Web Interface Access: Access the firewall's web-based management interface using a web browser and the provided credentials.
-
3. Configuration: This involves defining firewall rules to allow or deny specific traffic types. Rules are typically based on source IP address, destination IP address, port number, and protocol (e.g., allow web traffic on port 80, block access to specific websites).
-
Consult the documentation: Your firewall's documentation will explain the configuration process and available settings.
-
Consider professional help: If you're not comfortable with firewall configuration, consider seeking assistance from a qualified IT professional.
Additional Considerations:
-
Security Policies: Develop clear security policies outlining acceptable use of company resources and internet access.
-
Strong Passwords: Enforce strong passwords for all user accounts and change them regularly.
-
Ongoing Maintenance: Schedule periodic security audits to review your firewall configuration and ensure effectiveness. Enable automatic updates for firmware and threat signatures to stay protected against evolving threats.
Q. I need to hire IT professionals to manage my NGFW?
A: It depends on the firewall. If you're comfortable with basic IT tasks and have a user-friendly NGFW, you’ll be okay managing it yourself. Consider IT support for initial configuration, ongoing maintenance, or utilizing advanced features if you are using devices like the Palo Alto PA series.
Q. How many firewalls do I need?
A: Usually, one properly configured firewall at your internet gateway should do the job. Additional firewalls might be needed for large, geographically dispersed networks or to segment your network for enhanced security.
Q. How can I ensure my NGFW stays up-to-date with the latest threats?
A: Here are a few ways to ensure your NGFW is always protecting your network:
- Enable Automatic Updates: Turn on automatic updates for both firmware and threat signatures in your firewall settings.
- Schedule Security Audits: Regularly review firewall configuration, security policies, and user access controls (quarterly or annually).
- Employee Training: Educate your staff on cybersecurity basics like identifying phishing attempts, using strong passwords, and avoiding suspicious websites. This empowers them to be a first line of defense.
Q. Do I need to purchase additional hardware to run an NGFW?
A: Most NGFW appliances are self-contained meaning there's no need for additional hardware or software installation to get it working. You simply connect it to your network and configure it using a web interface or command-line interface. Exceptions include high-bandwidth environments or deploying redundant firewalls for critical operations.
How to Choose the Best Firewall for Your Business
Choosing the right firewall can be a complex decision, but it's an essential step in securing your business network.
Key Factors to Consider
- Security Needs:
What features are most important for your business? Deep Packet Inspection for comprehensive threat detection? Intrusion prevention to block unauthorized access attempts?
- Technical Expertise:
How comfortable are you and your team managing a firewall? User-friendly options are available for those with limited IT experience.
- Budget:
Determine how much you can realistically invest in a firewall solution.
- Team Size:
Smaller teams might benefit from simpler solutions, while larger teams might require more scalable options.
- Support:
Prioritize the level of support you need. Do you require 24/7 phone support, or is email support sufficient?
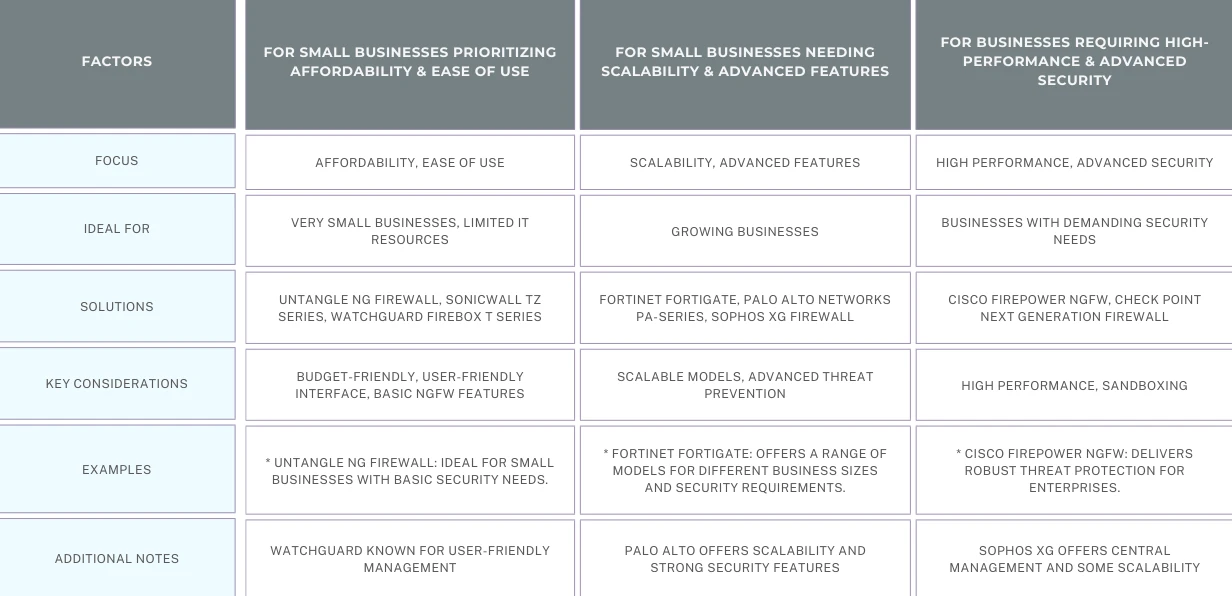
Making Your Decision
Once you've considered these factors, follow these steps to narrow down your options:
- 1. Match features to your security needs and budget.
- 2. Choose a user-friendly option if your technical expertise is limited.
- 3. Read online reviews to get insights into product quality and vendor support.
- 4. Contact vendors or resellers to get quotes tailored to your needs.
- 5. Consider a trial period (if available) to test out the firewall before committing.
Peace of Mind Starts Here
While investing in next-generation firewalls may require more planning, it can offer superior security for your business.
Ultimately, the best firewall choice depends on your budget, needs, and your company's IT expertise.
We hope this post simplifies the process of choosing the best firewall for your business.